About Me.
INSPIRED BY DIFFERENCE.
I have over twenty years of computer software, computer hardware, computer infrastructure, cybersecurity and other critically-related technology experience. I graduated from Queens College with a Bachelors in Sociology, focusing on data analytics, social psychology and behavior analysis. I am currently enrolled at the University of San Diego to obtain a Masters of Science in Cybersecurity Operations and Leadership, and plan to graduate in May, 2024. Click here to download my resume.
In 2012 I founded TeliApp, which has become an award winning NJ based technology solutions provider that delivers cybersecurity defense and Information Technology services to municipalities, public schools, public libraries, water and sewerage authorities. TeliApp develops meaningful insights and professional recommendations based on actionable data. TeliApp’s most recent awards include NJBIZ 2022 Companies to Watch, and govCIO Top 2022 & 2023 eGovernance Solution Provider. TeliApp is a Rising Star of the NJ Tech Council and is a repeat winner of software design and development awards from Clutch, including Global Leader Company, Clutch 1,000 Company, Leading UX Agencies, Leading Mobile App Developers, Leading NYC and Leading Philadelphia Software Development Firms.
Reference Link Library
A collection of essential online websites, periodicals and books that I feel are important or that I used and/or researched throughout the program.
Experience.
With each encounter, the brain sculpts neural pathways, etching a landscape of insight that guides future judgment.
01. TeliApp.
At TeliApp, my primary function is to help develop new business and recruit and excellent talent to work with us. I started TeliApp in 2012 and have loved going into work every day since. Our services include Cybersecurity Defense Training & Strategic Oversight, Information Technology (IT), Cloud Migrations & Administration for Email, Data & VOIP, Network Engineering, Wired & Wireless Network Infrastructure Installation & Maintenance, as well as Website Development & Content and Management.
02. JW Consulting.
From 2005 through 2011 I managed JW Consulting, where I leveraged my business relationships from my prior work experience to help emerging electronics companies find retail placement at big-box stores, including Walmart, Target, BestBuy, Staples and many others. In this role I was heavily focused on business development and operations, but also had to be on top of the latest consumer electronic trends to ensure a proper product fit.
03. 1-800-TOW-TRUCK.
IDT Corporation (NYSE:IDT) provided investment capital for the founding of this wholly owned subsidiary. As its CEO, from 1997 through 2005 my primary focus was developing new business and technology to help stranded motorists. The company was a national roadside assistance firm providing coverage in US, Canada & Puerto Rico. I provided strategic vision, tactical execution and wide-reaching daily management to drive growth momentum & achieve short & long range goals while meeting & exceeding budget objectives. I successfully launched Prepaid Roadside Assistance Cards in over 7,000 retail locations across the United States.
Cybersecurity Fundamentals
The artifacts presented here demonstrate my understanding of the professional and ethical responsibility of cybersecurity operations and leadership.
Reflections
The artifacts I selected delve into the realm of attack surfaces, offering valuable insights for any cybersecurity professional seeking to effectively manage risk. Examining the intersection of threats, vulnerabilities, and attack surfaces sheds light on where cyber risks reside and empowers us to develop comprehensive mitigation strategies. As we examine potential threats, from natural disasters to insider sabotage, we gain a practical understanding of how cybersecurity fundamentals translate into real-world scenarios. The papers I selected offer valuable insights for any cybersecurity professional, illuminating the multifaceted nature of risk and the necessity of comprehensive security strategies.
Having explored these concepts, I see their application in my cybersecurity career in many ways. Firstly, I will leverage this understanding of interconnected threats to conduct more comprehensive risk assessments, considering both physical and digital vulnerabilities. Secondly, I will advocate for the development and implementation of robust disaster recovery plans, ensuring my organization is prepared for any eventuality. Furthermore, I will communicate the importance of cybersecurity to stakeholders by highlighting its direct impact on brand reputation and customer trust. Finally, I will actively promote security awareness within my organization, recognizing the human element in information security.
Overall, this content serves as a valuable reminder that cybersecurity fundamentals are not theoretical concepts but practical tools for mitigating real-world risks. By applying these insights to my work, I will strive to contribute to building a more secure and resilient digital landscape for all. In particular, the following highlights any cybersecurity’s journey toward ensuring that one’s professional and ethical responsibilities are always intact and above board.
- Comprehensive Risk Assessments – I will strive to conduct thorough risk assessments, considering both technical vulnerabilities and social engineering risks posed by various attack vectors.
- Advocate for Robust Defenses – The importance of comprehensive disaster recovery plans and security awareness training will be emphasized in my work, recognizing the interconnected nature of threats.
- Effective Communication – Highlighting the impact of cybersecurity on brand reputation and customer trust will be crucial for securing buy-in from stakeholders.
- Continuous Learning – Recognizing the evolving nature of cyber threats, I will remain committed to continuous learning and upskilling to adapt and mitigate emerging risks.
Cryptography
Cryptography is a crucial tool for keeping information and systems safe. While we explored the core components of cryptography, our main focus was how it helps enforce essential security policies, such as authentication, confidentiality, and data integrity. We learned about essential concepts such as stream and block ciphers, hashing, encryption methods and key exchanges.
Reflections
The exercise exposed me to the elegant beauty and intricate dance between theoretical concepts and practical implementation. The Chinese Remainder Theorem, once a theorem confined to textbooks, took on a new life, its mathematical precision harnessed to tackle the very real problem of key recovery. Witnessing how beautifully precise mathematics could unlock solutions in such a complex and critical domain instilled a profound appreciation for the power of cryptography. Moreover, the exercise served as a potent reminder that the elegance of mathematics doesn’t negate the inherent complexities of its application. The challenges surrounding key management, which include compromise, theft, and storage failures, painted a vivid picture of the delicate balance needed in real-world cryptography. Each theoretical solutions present their own set of ethical and practical considerations, forcing me to think critically about the trade-offs involved.
This newfound understanding will significantly impact my professional trajectory. As I interact with clients in the future, the insights gained from this exercise will empower me to address their cryptographic needs with greater awareness and responsibility. Now, I can delve deeper into the challenges of key management, exploring solutions within their specific contexts while acknowledging ethical and risk-management implications. For instance, when advising a client on data encryption strategies, I can now go beyond simply recommending algorithms and instead discuss the complexities of key escrow and recovery options. I can discuss the potential benefits and drawbacks of each approach, ensuring they understand the trade-offs before making informed decisions. Additionally, I can contribute to internal discussions and policy creation within my organization and that of my clientele, bringing a well-rounded perspective that considers both the technical intricacies and the ethical implications of cryptographic practices.
Security Architecture
Security architecture artifacts serve as invaluable maps and guideposts, ensuring consistency and traceability throughout the intricate journey of security design. These documented representations of the security strategy, like threat models, security requirements, and network diagrams, provide a shared understanding for all stakeholders involved. This shared lens fosters consistency, as everyone utilizes the same blueprint when making security decisions, minimizing the risk of conflicting approaches. Additionally, these artifacts create a clear audit trail, allowing for transparent communication of design rationale and facilitating future modifications based on evolving threats or technology advancements.
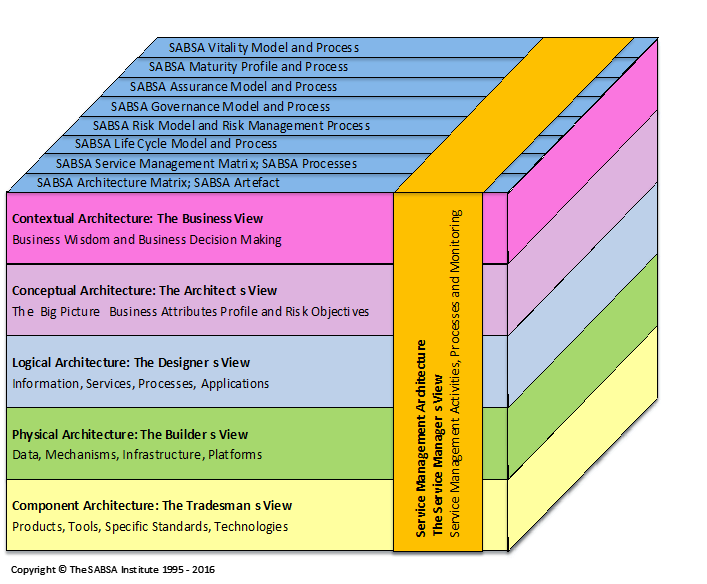
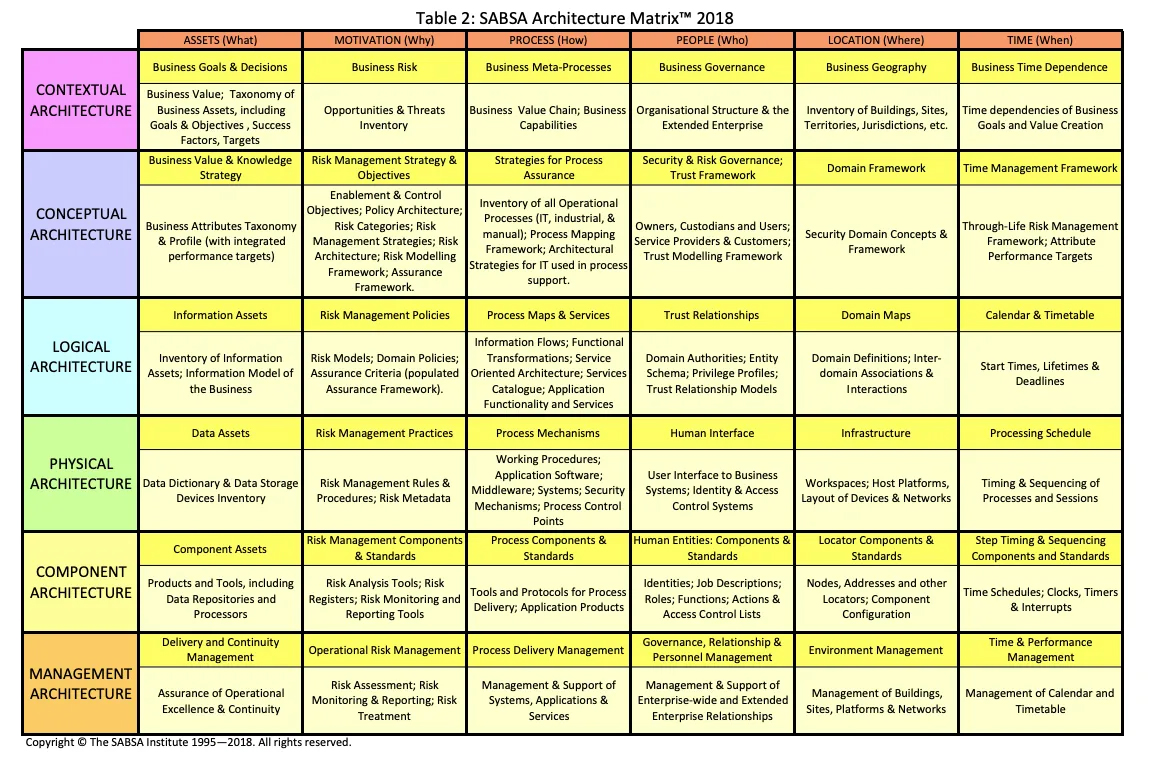
The five main SABSA Layers form a hierarchical framework that seamlessly connects business context into actual security implementation. The Contextual Layer establishes the foundation, outlining the organization’s vision, goals, and risk tolerance. This feeds into the Conceptual Layer, which defines the strategic approach to security, aligning it with business objectives. The Logical Layer then translates this approach into concrete architectural elements, such as network diagrams and system specifications. The Physical Layer focuses on tangible components like hardware and software, ensuring that they align with the logical design. Finally, the Management Layer governs the entire process, including policies, procedures, and performance monitoring, ensuring ongoing effectiveness and compliance. This layered structure allows for a top-down, yet interconnected, approach, effectively translating high-level business objectives into practical security controls and practices.
I am truly grateful that for me, this course highlighted the power of applying theoretical knowledge to tangible projects in my professional work, directly impacting the real-world security landscape. It underscores the value of relevant coursework and the serendipitous synergy that can enable immediate and practical value.
Reflections
The SABSA model defines interconnected layers that guide the development and implementation of an enterprise security architecture. Each layer focuses on a specific aspect of security, and together they provide a comprehensive view of how security should be integrated into an organization’s overall architecture that can be used to build a holistic and integrated security architecture that effectively protects their critical assets and aligns with their business objectives. The SABSA model provides a comprehensive security framework and helps ensure that security is fully integrated into the overall enterprise architecture.
During this course, a unique opportunity arose that perfectly aligned with my professional work. At work, we are developing a novel software platform for local governments, aiming to completely digitize their procurement process. While the framework and functionality were solidified, moving to development hinged upon a key requirement – a comprehensive security architecture document. Fortunately, the course curriculum employed the SABSA framework, focusing on crafting intelligent and adaptable security models. These elements were crucial for our own platform, which needed to not only ensure security but also accommodate future growth and evolving threats. The assignments (and chosen artifacts for this section), centered around crafting security architectures for a fictional government entity, which proved to be serendipitous. The theoretical exercises directly translated into valuable real-world application for my work.
This fortuitous overlap allowed me to seamlessly bridge the gap between academic pursuit and professional needs. The knowledge and skills gained through the course, specifically the expertise in utilizing the SABSA framework, were immediately put to use in crafting the vital security architecture document for our platform. This document forms the bedrock upon which our secure and adaptable software could be built, ultimately serving the critical needs of local governments. My work in this course not only demonstrates my technical skills but also reflects my commitment to professionalism and ethical practices in security architecture, ensuring responsible and sustainable security measures for our groundbreaking platform and future endeavors.
Cybersecurity Law & Policy
Cybersecurity law and policy are the foundation for protecting information systems, data, and critical infrastructure from cyberattacks. They establish guidelines for data privacy, breach notification, and security standards. Policies translate these legal requirements into actionable steps for organizations. Understanding and implementing them is crucial because they ensure that organizations comply with legal mandates, avoiding regulatory fines and reputational damage, and also because they minimize security risks by outlining best practices for data protection, access controls, and incident response.
Reflections
My Cybersecurity Law & Policy class has been an eye-opening experience. Analyzing real-world cases such as the MGM hack (2023), the Guccifer case (2016), and the Bangladesh Bank Heist (2016) highlighted the crucial connection between legal requirements and effective cybersecurity practices. Weaknesses in access controls and incident response, as seen in the MGM hack, can have devastating consequences. Poor communication between IT and InfoSec can create vulnerabilities that threat actors can exploit, as we learned while analyzing the Bangladesh Bank Heist. This class emphasized the importance of mapping every aspect of an organization’s cybersecurity strategy, from policies to procedures, to a legal foundation.
Analyzing current and past cybersecurity litigation offers invaluable lessons, because we can identify potential weaknesses in our own defenses and prevent similar vulnerabilities from being exploited by understanding the legal reasoning behind judgements. Tracking evolving cybersecurity legislation, encompassing data privacy laws (federal, state, and international), and local and international cybersecurity regulations, ensures our organization remains compliant. This proactive approach minimizes legal risks and potential penalties. Understanding digital forensics best practices becomes vital in the unfortunate event of litigation. Following proper evidence collection and preservation procedures prevents evidence spoliation, which could otherwise weaken an organization’s legal standing and potentially disqualify expert witnesses.
Both the class’s subject matter and my incredible instructor instilled in me the importance of tailoring cybersecurity frameworks to an organization’s specific mission and legal obligations. Frameworks such as NIST CSF provide a strong foundation, however, true effectiveness comes from customization. This knowledge will make me a more effective cybersecurity professional in several ways. I can now advocate for robust defenses that address compliance needs and minimize risk. I’m committed to promoting ethical practices that respect user privacy and adhere to legal frameworks. I also learned how to bridge the gap between legal and technical teams by effectively communicating compliance requirements, fostering a more comprehensive security posture across the organization. Cybersecurity Law & Policy class has educated me with the legal knowledge and strategic perspective I require to navigate the evolving cybersecurity landscape as a more effective professional and ethical cybersecurity leader.
Risk Management
The National Institute of Standards and Technology (NIST) developed the Risk Management Framework (RMF) to address the need of proactive cybersecurity risk management within the US government. RMF provides a systematic process for translating theoretical risk management principles into a practical approach for cybersecurity professionals by identifying, assessing, and mitigating cybersecurity risks. Information security professionals utilize RMF to prioritize efforts by systematically identifying potential weaknesses in computer systems and networks, and by analyzing the likelihood and impact of potential threats exploiting those weaknesses.
Reflections
This course shatters any naive illusions that hardware alone can properly defend an organization from cybersecurity threats. People play a major role. Cybersecurity risk management is an ongoing balance between proactive preparation and reactive response with far-reaching consequences. Risk management is not a one-time audit or checklist; rather, it is a dynamic process that requires continuous monitoring and adaptation. Identifying and prioritizing vulnerabilities is never enough. In addition, information security professional must translate those findings into actionable steps, allocating resources effectively to mitigate the most probable and damaging threats.
This course emphasized to me that effective risk management necessitates clear and proactive communication and collaboration across all levels of an organization. Information security professionals must translate complex technical jargon into actionable plans for management to understand and endorse. Equally important is educating staff about cybersecurity best practices to foster a culture of security awareness.
I see myself incorporating this knowledge into my professional life in several ways. First, I will prioritize ongoing risk assessments, using frameworks like NIST’s RMF to systematically identify and address vulnerabilities. Second, I will champion a culture of risk awareness within my team, fostering open communication and encouraging everyone to report suspicious activity. Third, I will advocate for a balanced approach to security spending, ensuring we have the necessary resources without becoming wasteful.
Ethical considerations must always remain at the forefront of my decision-making. When vulnerabilities are discovered, I will strive for a balance between transparency and responsible disclosure, working with vendors to develop timely patches before information regarding vulnerabilities can be weaponized. This commitment to ethical conduct reflects my understanding that cybersecurity is more than just protecting systems; rather, it is about safeguarding the privacy and well-being of individuals and organizations alike. This knowledge empowers me to become a more effective cybersecurity professional, one who actively manages risk and properly defends against threats.
Management & Cybersecurity
While cybersecurity professionals identify and address technical vulnerabilities, strong management practices ensure these efforts are successful. In this course, I learned about the fundamental principles that bridge this gap, exploring the economic considerations of cyber threats, strategic staffing decisions, resource allocation strategies, effective communication channels, and responsible acquisition practices. By understanding these key areas, managers can empower security teams and build a more resilient organization to combat against threats.
Reflections
The Request for Proposal (RFP) project for BioHuman Corporation’s cybersecurity awareness training program served as a critical learning experience, highlighting the profound interconnection between effective management and robust cybersecurity. While I initially viewed these areas as separate entities, this course revealed how their synergy is paramount.
This project shed light on the economic considerations of cybersecurity, and elucidates the need for management to conduct cost-benefit analyses when evaluating cybersecurity investments. Balancing security needs with budgetary constraints will be a crucial aspect of my future professional endeavors. The project also teaches that a one-size-fits-all approach to cybersecurity awareness is ineffective. Cybersecurity awareness training programs must target not only employees but also clients, partners, and vendors – anyone – with access to their systems. This recognizes that an organization’s security posture is only as strong as its weakest link. Incorporating this knowledge into my professional life means advocating for training programs that cater to diverse audiences with varying levels of technical expertise. Developing this RFP also reminded me about the importance of clear communication and collaboration between management and security teams. Effective communication will be essential in ensuring alignment between internal goals and the chosen vendor’s capabilities.
Beyond technical considerations, this course reinforced in me the importance of ethical conduct in both management and cybersecurity practices. Emphasis on data security, ownership, and responsible use aligns with core ethical principles. As a professional, I acknowledge the ethical implications of managing sensitive data and the importance of adhering to relevant regulations and frameworks, such as HIPAA or NIST SP 800-39.
Finally, the RFP development process itself served as a valuable exercise in professionalism. Following specific formatting and submission guidelines, meeting deadlines, and presenting information in a clear and concise manner are all hallmarks of professional conduct. Applying these principles to future projects, reports, and client interactions will demonstrate professionalism and enhance credibility.
Secure Software Design & Development
Robust cybersecurity strategies are critical safeguards for any organization. A cornerstone of this strategy is the Information Systems Security Plan (ISSP), which outlines an organization’s comprehensive approach to protecting its information systems and data. Developing, implementing, and actively utilizing an ISSP includes technical security measures, but also encouraging a culture of professional and ethical conduct around cybersecurity practices, ensuring everyone within the organization understands their role in mitigating cyber risks.
Reflections
Prior to exploring secure software design and development (SSDD), I viewed software creation as a functional endeavor. This course reveals the critical role SSDD plays in safeguarding systems and data, and how simply writing code that works is insufficient; rather, building secure code from the ground up is paramount. This course will significantly impact my professional approach to software development. Implementing a structured framework ensures that security is built into the development process. This commitment to a secure SSDD not only reflects professionalism but also demonstrates an ethical obligation to create trustworthy software.
One of the most impactful insights has been the concept of threat modeling. Identifying potential vulnerabilities early in the development lifecycle is crucial for mitigating risks proactively. By considering how attackers might exploit weaknesses, we can design software with built-in defenses. This proactive approach not only strengthens the final product but also saves time and resources compared to fixing vulnerabilities after deployment.
The emphasis on secure coding practices also resonated. Understanding common coding errors that create security vulnerabilities allows me to focus on making sure that our team writes clean, secure code. Utilizing static code analysis tools and adhering to secure coding principles will become an integral part of my frm’s software development process.
The ethical considerations of secure software development are so important. Software vulnerabilities can have far-reaching consequences. Releasing insecure software not only exposes users to risk but also erodes trust in developers and the software development community as a whole. By prioritizing SSDD principles, we take responsibility for the potential impact of our work. Building secure software demonstrates respect for users’ privacy and data security. Secure software development is just as much about building functional code as it is about building trust, ensuring reliability, and safeguarding the code that we release.
Network Visualization & Vulnerability Detection
Network Visualization and Vulnerability Detection are two critical tools used by Network Defenders. Network Visualization acts as a digital map by offering a comprehensive view of all connected devices and their interactions within a network, which enables security professionals to identify potential weaknesses, optimize network performance, and troubleshoot issues efficiently. Vulnerability Detection, on the other hand, takes a more proactive approach, by actively scanning networks for exploitable weaknesses in software, hardware, or configurations. By pinpointing these vulnerabilities, security teams can then prioritize remediation efforts and prevent attackers from exploiting these weaknesses. Both Network Visualization and Vulnerability Detection tools can be used ethically for penetration testing, a process in which authorized security professionals attempt to exploit vulnerabilities to assess the effectiveness of existing security measures. This proactive approach helps organizations identify and address weaknesses before malicious actors do.
Reflections
Network Visualization and Vulnerability Detection are powerful tools that, when used ethically and professionally, form the cornerstone of a robust cybersecurity strategy. This course provided many insightful revelations about technology systems and the professional cybersecurity challenges that lay ahead. Every cybersecurity software tool will likely have its own unique characteristics, and the challenges encountered may likely be a result of variables such as the operating systems used, and a myriad of networking parameters. The challenges that I encountered were mostly technical, learning about the nuanced characteristics of each software tool and the variables that create challenges.
The goal of any educational endeavor is not merely the pursuit of knowledge for the sake of knowledge, but rather to gain knowledge not possible to acquire in the work environment, and/or to obtain the academic background required to properly perform certain job functions in the workplace (Biesta, 2009). Perhaps the most significant milestone, discovery and revelation moment for this emerging cybersecurity professional was to lean into these technical challenges. This lesson can be applied to any circumstance in which the professional is otherwise tempted to choose a path of least resistance.
The power of network visualization and vulnerability detection tools comes with significant professional and ethical responsibilities. Professionally, we have a duty to leverage these tools effectively to create a comprehensive picture of the network landscape, which requires ongoing analysis and adaptation to keep pace with evolving threats and network configurations. Prioritizing vulnerabilities based on risk and implementing appropriate remediation strategies demonstrates responsible use of these tools. Ethically, the principle of trust is paramount. The data gleaned from network visualization and vulnerability detection tools grants us visibility into the very core of an organization’s digital infrastructure. This trust necessitates using this information solely for legitimate cybersecurity purposes. Transparency in vulnerability disclosure to vendors and responsible authorities is crucial. Utilizing Network Visualization and Vulnerability Detection ethically and professionally strengthens trust within the organization and fosters a strong and proactive cybersecurity posture.
Cyber Threat Intelligence
Reactive defense is not sufficient to protect technology infrastructure. Organizations require a proactive approach to anticipate attacker strategies and bolster their defenses. Cyber Threat Intelligence embodies proactive cybersecurity, encompassing the collection, analysis, and dissemination of actionable intelligence on potential cyber threats. By understanding the motivations, tactics, and techniques (TTPs) of cyber adversaries, organizations can proactively identify vulnerabilities, prioritize remediation efforts, and implement targeted defenses.
Reflections
The professional and ethical application of cyber threat intelligence cannot be understated. Professionally, security teams leverage CTI to make informed decisions about resource allocation and security investments, which empowers them to focus on the threats that pose the greatest risk to the organization’s specific assets and objectives. However, the ethical considerations are equally important. Gathering and utilizing CTI responsibly requires adherence to legal and ethical frameworks, respecting intellectual property rights and data privacy regulations. Responsible disclosure practices in which discovered vulnerabilities are reported to vendors and authorities, are essential for mitigating threats to the broader cybersecurity ecosystem. A well-developed CTI program, applied with both professional expertise and ethical grounding, empowers cybersecurity specialists to transform the organizations they defend from reactive victims to proactive defenders in the cyber realm.
The continued growth of cyber-related attacks on critical infrastructure requires a strong cyber security culture to be a part of any organization’s cyber defense strategy (Pătrașcu, P. 2019, p. 273). The goal of any CTIP is to introduce, discuss, and review cyber threat intelligence and to incorporate it into the operations of the InfoSec team, as part of a holistic approach to information security designed to protect an organization from a cybersecurity incident, such as a ransomware attack. Resolving cybersecurity concerns is not a ‘one size fits all’ or ‘one and done’ process. To properly protect an organization’s technology infrastructure, its data, email and personnel from cyber-related threats, its cybersecurity posture will need to continue to evolve, just as the cyber threat landscape continues to evolve. This is only made possible through the development of a strong and practical cyber threat intelligence plan.
On a personal note, the world of cyber threat intelligence isn’t all about dry reports and technical jargon. I will admit that there is an undeniable thrill unraveling the mind of a cyber attacker. By meticulously analyzing past attacks, malware code, and online chatter, CTI professionals become digital detectives, piecing together the motivations, tactics, and tools used by adversaries. I find this type of intellectual challenge, akin to solving a complex puzzle, highly rewarding. Predicting an attacker’s next move based on historical patterns and emerging trends adds another layer of excitement. Imagine successfully anticipating a phishing campaign or identifying a vulnerability before it can be exploited, and the satisfaction felt after outsmarting cybercriminals. It is important to remember though that CTI is not a game. This intellectual pursuit has real-world consequences. By understanding attacker behavior, CTI professionals can safeguard critical infrastructure, protect sensitive data, and ultimately contribute to a more secure digital landscape.
Incident Response & Computer Network Forensics
Incident response focuses on containing an attack, minimizing damage, and eradicating the threat, which involves identifying the breach point, isolating compromised systems, and restoring functionality. Following the initial response, computer network forensics meticulously examines digital evidence to reconstruct the attack timeline, identify the culprit, and gather potential legal evidence. This meticulous work helps organizations understand attacker methods, improve future defenses, and potentially hold malicious actors accountable. Together, incident response and computer network forensics enable organizations to not only recover from an attack but also learn from the attack, which strengthens the organization’s cybersecurity posture.
Reflections
The final project on incident response and network forensic investigation provided a deeper understanding of crucial cybersecurity practices, and also highlighted the significance of professional and ethical conduct in their application. By continuing to hone my ability to collect, analyze, and preserve digital evidence, I become more adept at reconstructing attack timelines, identifying the culprit’s methods, and gathering potential legal evidence. Our training emphasized the development of clear, concise, and defensible reports that can be understood by both technical and non-technical audiences; this can be challenging. These reports are instrumental in informing remediation efforts, implementing stronger security controls, and potentially prosecuting cybercriminals.
This course helped solidify my grasp of the incident response lifecycle and emphasized the vital role of network forensics in post-incident analysis. Learning to collect, analyze, and preserve digital evidence will be instrumental in reconstructing attack timelines, identifying attacker methods, and potentially gathering legal evidence. These skills are essential for mitigating future risks and holding malicious actors accountable. This course also dealt with serious professional and ethical considerations surrounding incident response and network forensics. The importance of maintaining a chain of custody for digital evidence and adhering to data privacy regulations became abundantly clear. Understanding the legal implications of these practices ensures responsible handling of sensitive information. I plan to continuously update my skills using digital forensics tools and techniques, because staying abreast of evolving technologies and methodologies will ensure the ability to effectively investigate even the most sophisticated cyberattacks.
This course equipped me with the practical skills of incident response and network forensics while clearly expressing the professional and ethical considerations that accompany their application. I am confident that I can leverage this knowledge to contribute to a more secure digital environment, both in my professional endeavors and by advocating for best practices within the organizations I serve.







